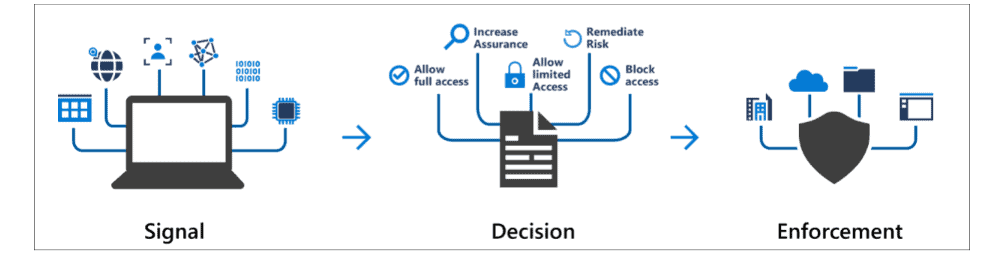
eGroup | Enabling Technologies has helped many organizations properly plan out and implement their conditional access policies. With the right foundation and framework, you can be confident that your Azure AD environment is setup to adhere to Zero Trust principles.