Azure Sentinel Hunting

Hunting Overview
Azure Sentinel Hunting is based off queries. It allows for manual, proactive investigations into possible security threats based on the ingested data as well as retroactive pursuits of attacks and root cause analysis. Hunting consists of several capabilities:
Queries are based on Kusto Query Language (KQL). These can be very simple queries to extremely complex, specific use case scenarios. To get started, in the Azure Sentinel Portal, go to Hunting. You can run one or all the built-in queries or click New Query to create a new custom query.
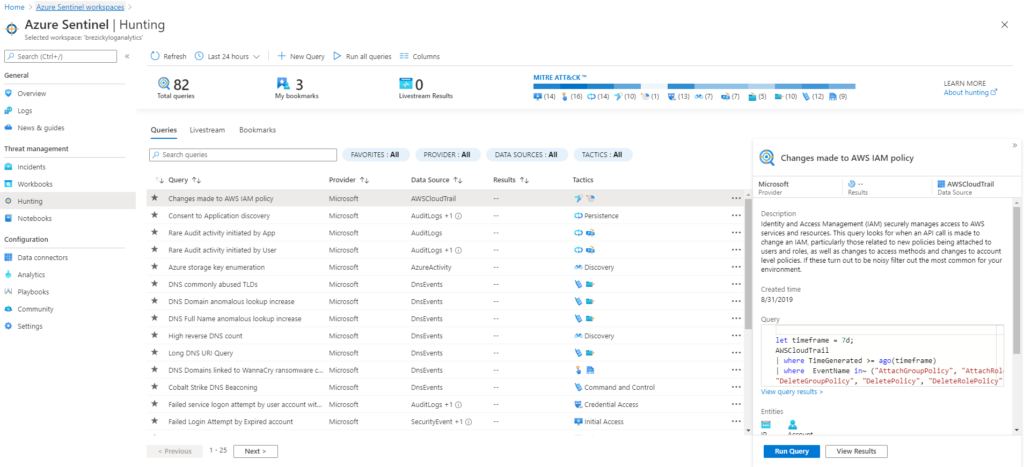
When building a query, if you are not familiar with the data types available in Azure Sentinel, you can use the left side of the page to view the available tables and filters to assist with creating the correct query. While typing, you are provided an ISE-like experience to help define your query. In addition to the built-in queries provided by Microsoft, there are many examples on GitHub and other online sources. Having some idea of what you are hunting will help draft these queries.
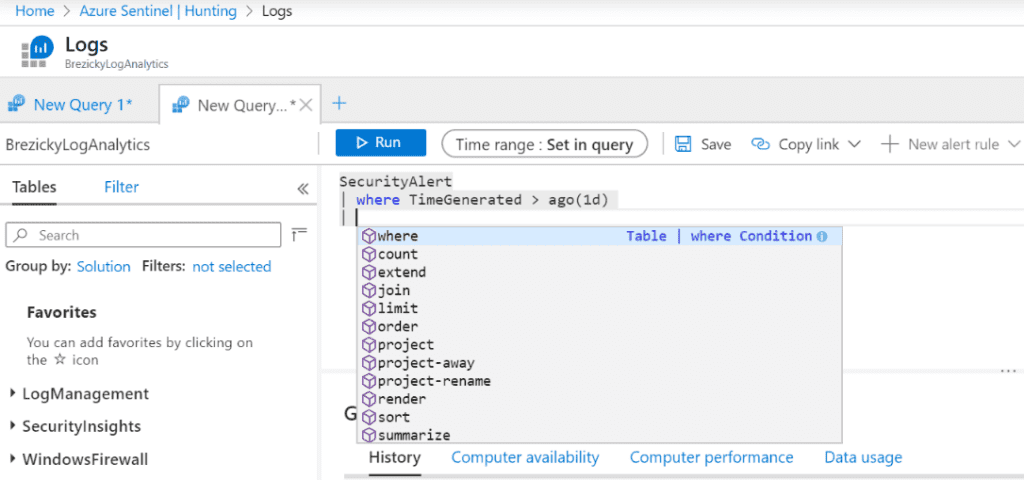
Live Stream
While queries help discover activity that has already occurred and ingested, hunting using live stream allows you to create an interactive session and actively run queries to find any activities you are searching for, malicious or not. When an alert occurs, you will receive an Azure Portal notification. Each session can also be used to create an analytic alert rule by clicking Elevate to alert.
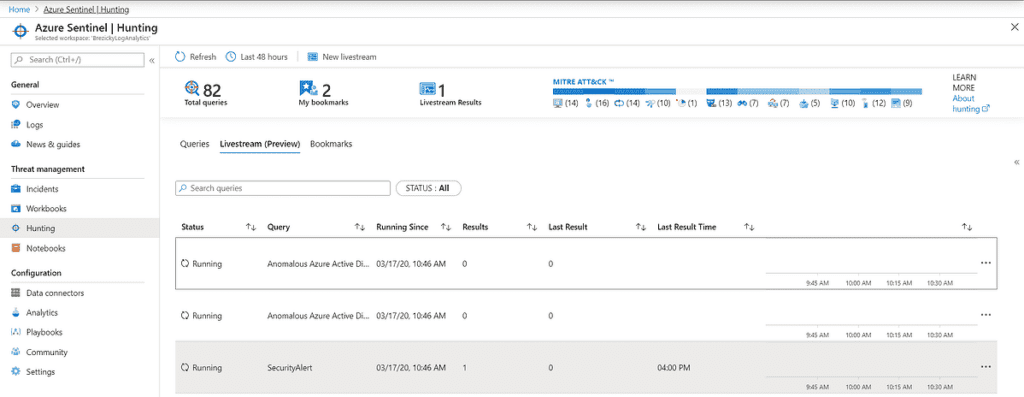
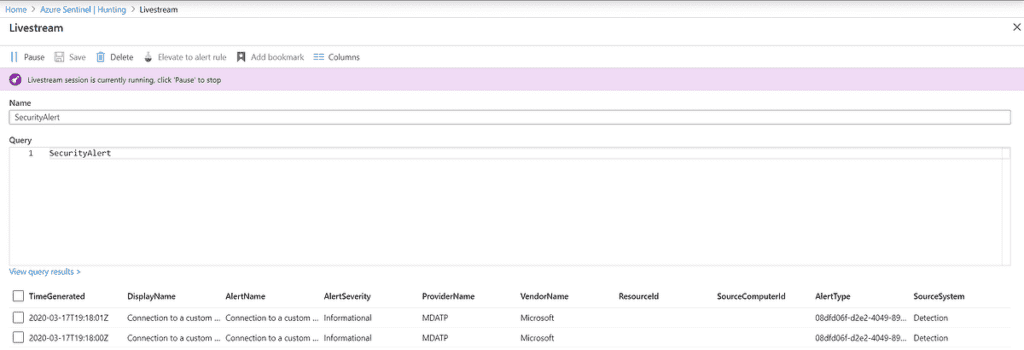
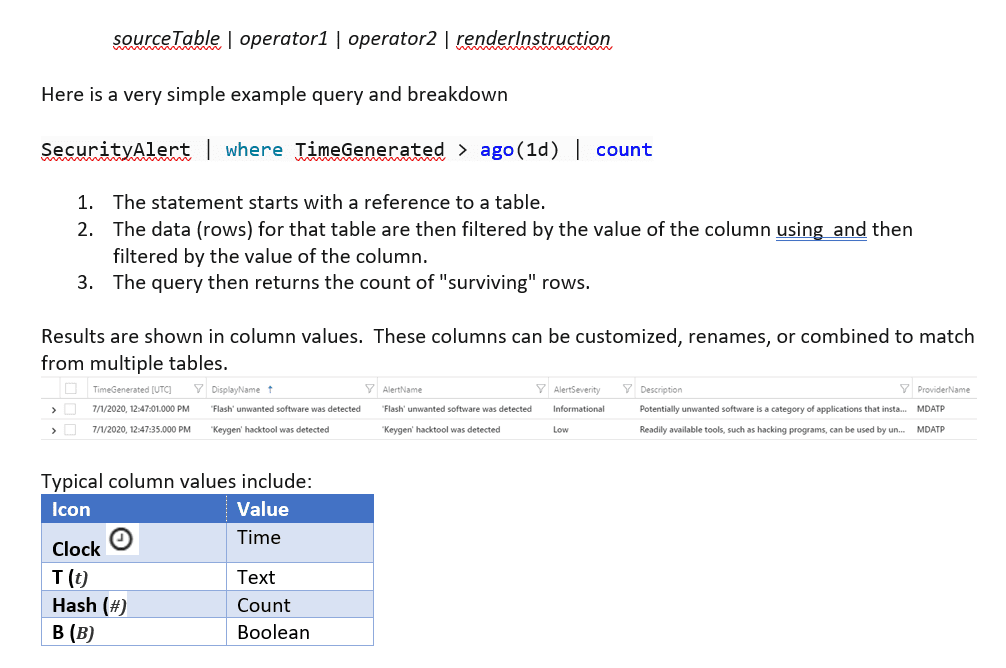
Query Creation
At some point in your Azure Sentinel journey, the built-in and community provided queries may not meet your organizational requirements or provide the specific use case scenario you are hunting for. You will have to create a query for yourself. Azure utilizes KQL or Kusto Query Language. A KQL query is a read-only request to process data and return results.
Azure Sentinel and KQL make use primarily of Tabular expression statements, which is a composition of data sources (Tables), data operators (filters such as where), and rendering operators (such as count). Each request is separated by the pipe character (|). Most of the syntax, particularly the tables, are case-sensitive.
Query Best Practices
Creating your own queries from scratch can be a daunting and intimidating task. The following suggestions are best practices to get started creating queries from scratch. There are many best practices as well as other preferred ways to go about creating queries. While these certainly apply to all queries, simply and complex, these are meant for those who are just starting to learn the language and will help to prevent an overwhelming feeling of complexity until you are more comfortable with the language.
Hunting can be a powerful way to provide valuable insights across all your organization’s data sources. Microsoft has done a great job providing numerous built-in capabilities with over 80 default hunting queries and 100’s of example queries within Log Analytics Queries. Community resources, such as GitHub, provide many additional customized, scenario-based queries. Chances are, you will not need to create any custom or unique query of your own as you are building out your cloud SIEM solution.
However, if you do wish to have some guidance and assistance, eGroup | Enabling Technologies can help you properly prepare for moving to the cloud based on Microsoft Best Practices and utilizing a secure and productive environment. You can check out more in the Azure Migration Services section of our website.
Contact our team of experts today to learn more about Microsoft solutions and cloud storage.
Last updated on July 31st, 2023 at 11:44 am