Azure Sentinel Operations

Introduction
Now that Azure Sentinel has started collecting data, it’s time for a deep dive into each component to discover how to utilize the data. The examples below are sample use cases of what Azure Sentinel can do. It is by no means an extensive overview of the capabilities. There is a massive amount of potential available.
Always start simple with the built-in features Microsoft provides. Start with specific scenarios or risks you wish to monitor. Then build onto that with more advanced, specific queries as you identify potential threats that are impacting your organization. This blog outlines some sample use cases from the following components:
Workbooks
Workbooks allow you to take the data ingested into Azure Sentinel and visualize what it looks like. There are built-in templates provided by Microsoft and custom workbooks can be created. Workbooks can provide quick wins, since they’ll provide logical insights without requiring Sentinel expertise.
One such template is the Exchange Online Workbook, showing insights on email activities within the tenant. The following is an example of potential suspicious activities to investigate.
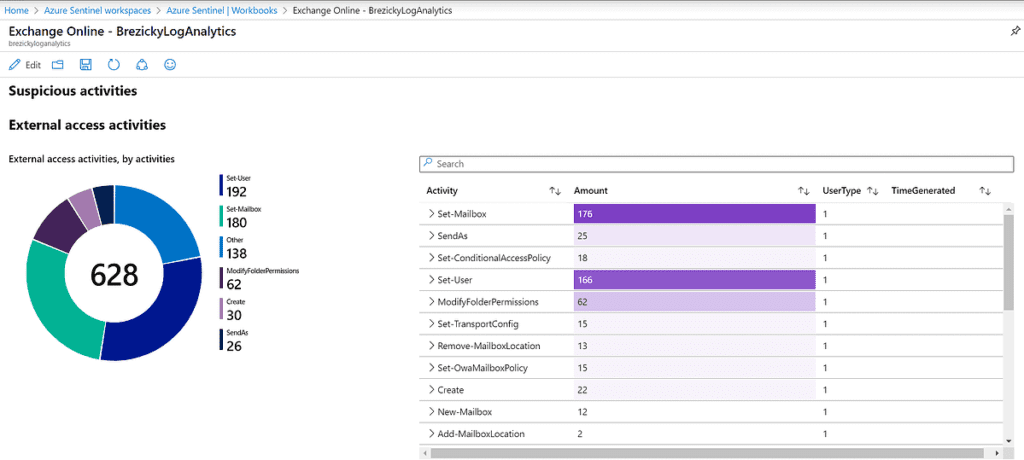
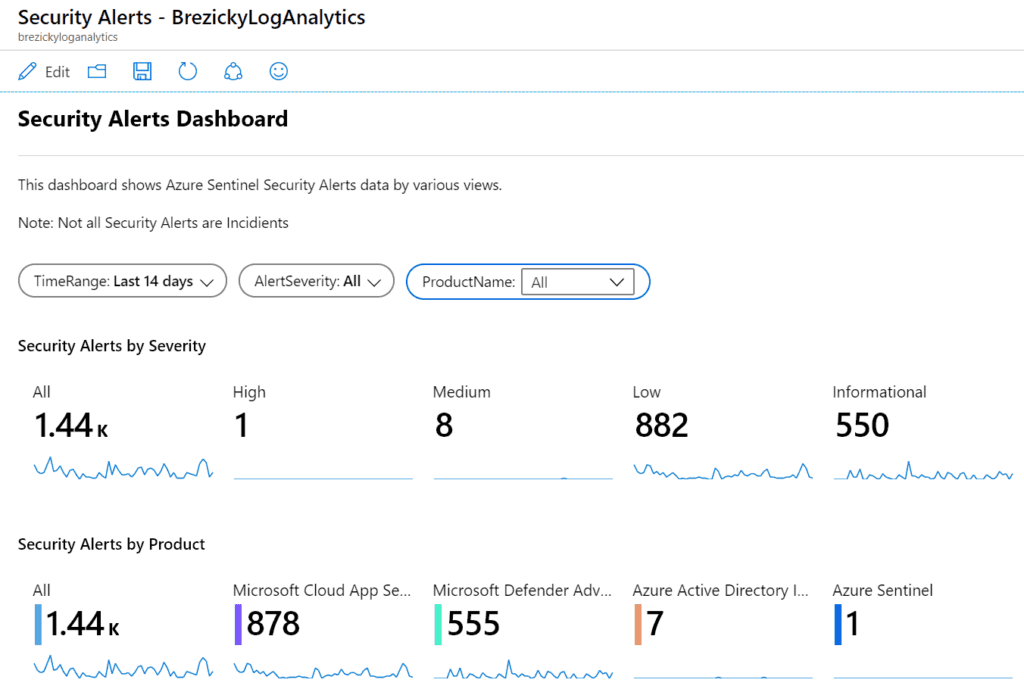
Another template, the Security Alerts workbook, provides a holistic view of where alerts are coming from and their overall severity. This can help identify where a lot of noise may be coming from and allow further investigate or modification of existing policies to reduce false positives.
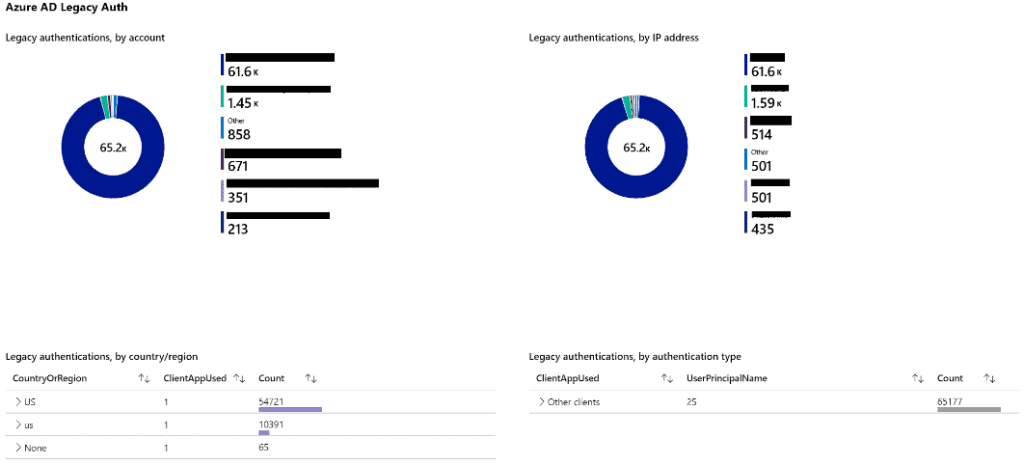
Microsoft is disabling legacy authentication on Oct. 13, 2020 for several protocols. You can use the Insecure Protocols workbook to capture existing legacy authentication attempts to plan on migrating to Modern Authentication. This workbook can account for both Microsoft Entra ID (formerly Azure AD) and on-premises Active Directory authentication.
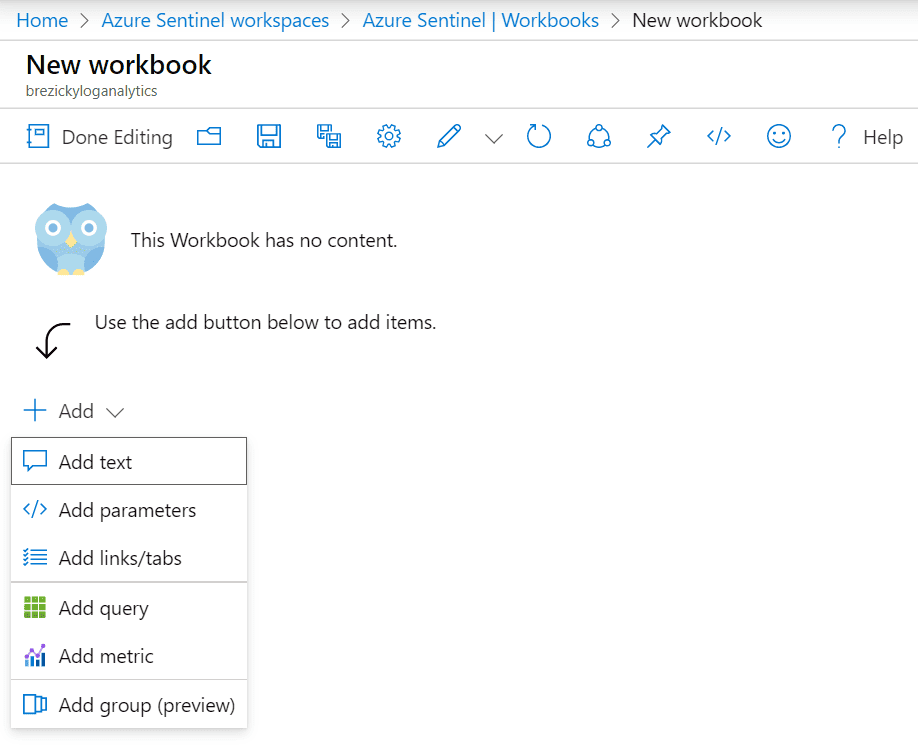
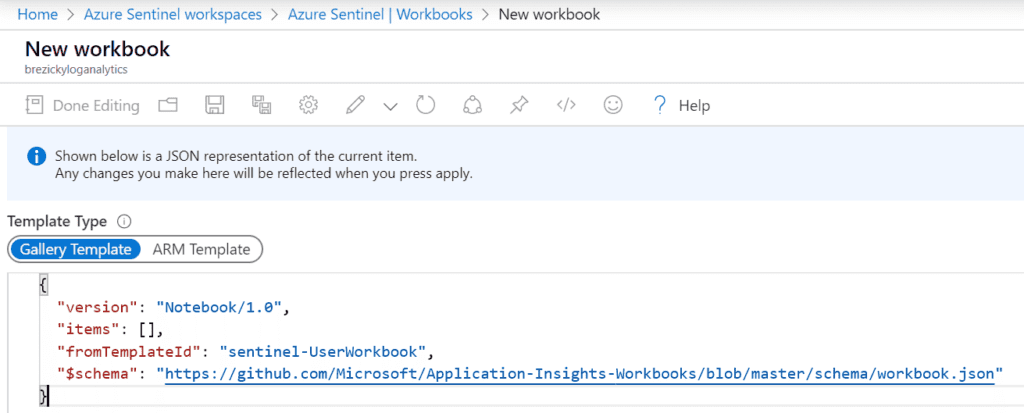
Custom workbooks can be created to provide the exact insights you are looking for. You can add several different components including text labels, parameters for resource picker searches, and links and buttons for actions. Queries and metrics can be added for further customization. Finally, using the advanced editor, you can import Gallery or ARM templates to create the workbook from JSON code.
Hunting
For advanced Security Operators and IT Pros, hunting allows proactive assessments against specific risks. They allow manual, proactive investigations into possible security threats based on the ingested data. Hunting is based off queries. Microsoft provided several built-in queries and custom queries can also be created. Once a query is created you can convert it into an analytic rule to run on a schedule.
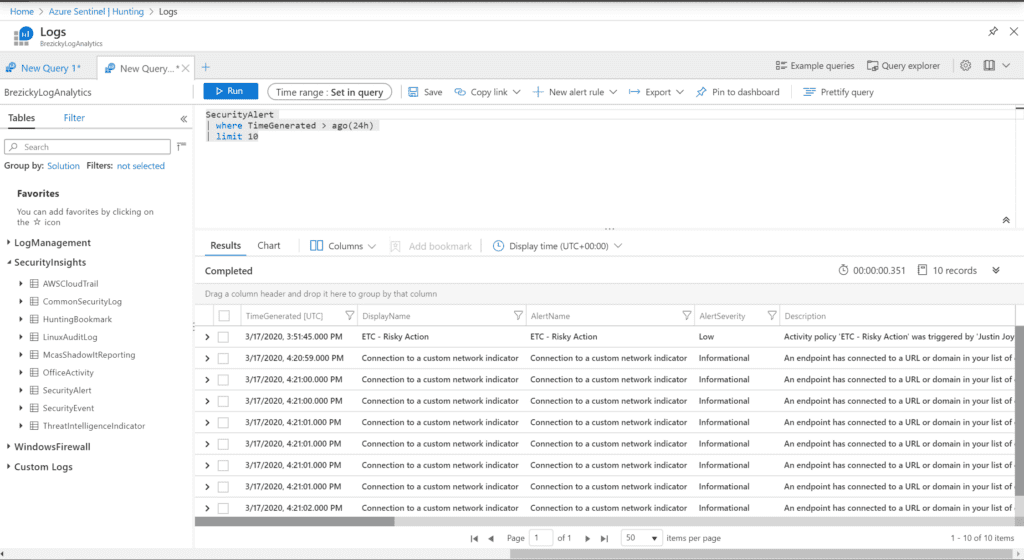
Sample queries can also be obtained from each data connector page.

Analytics
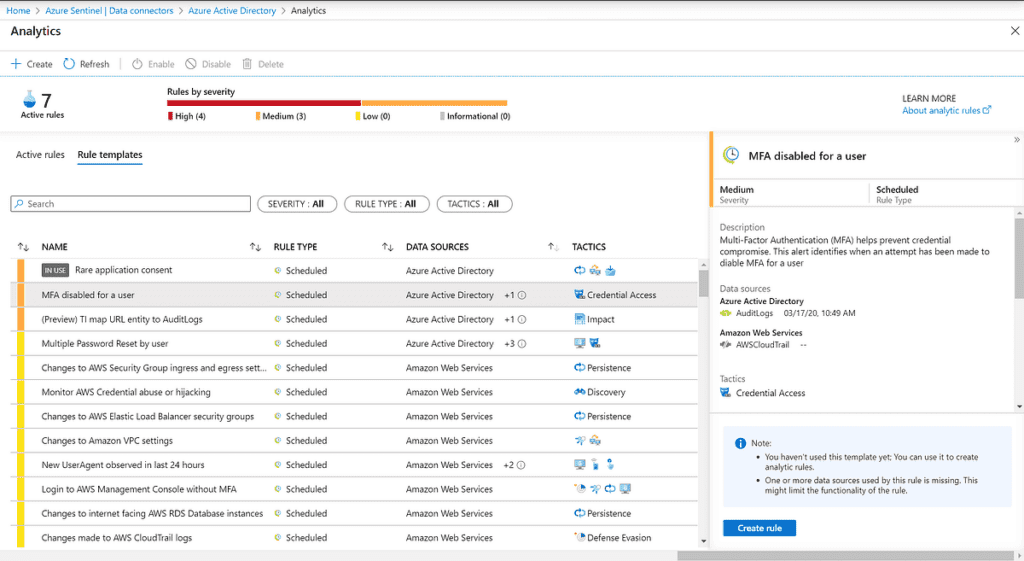
Once you have a solid query created, you can create an analytic alert rule to perform additional actions on those results. As with most other components of Azure Sentinel, Microsoft has also provided built-in analytic template rules with pre-created queries based on the data sources. You simply need to select the template and click Create rule.
During the creation of a template or custom analytic rule, you can configure specific settings to create an appropriate schedule and alert threshold. You can specify how often to run the query and how far back to search. In additional, alert threshold specifies how many results are required to issue an incident alert.
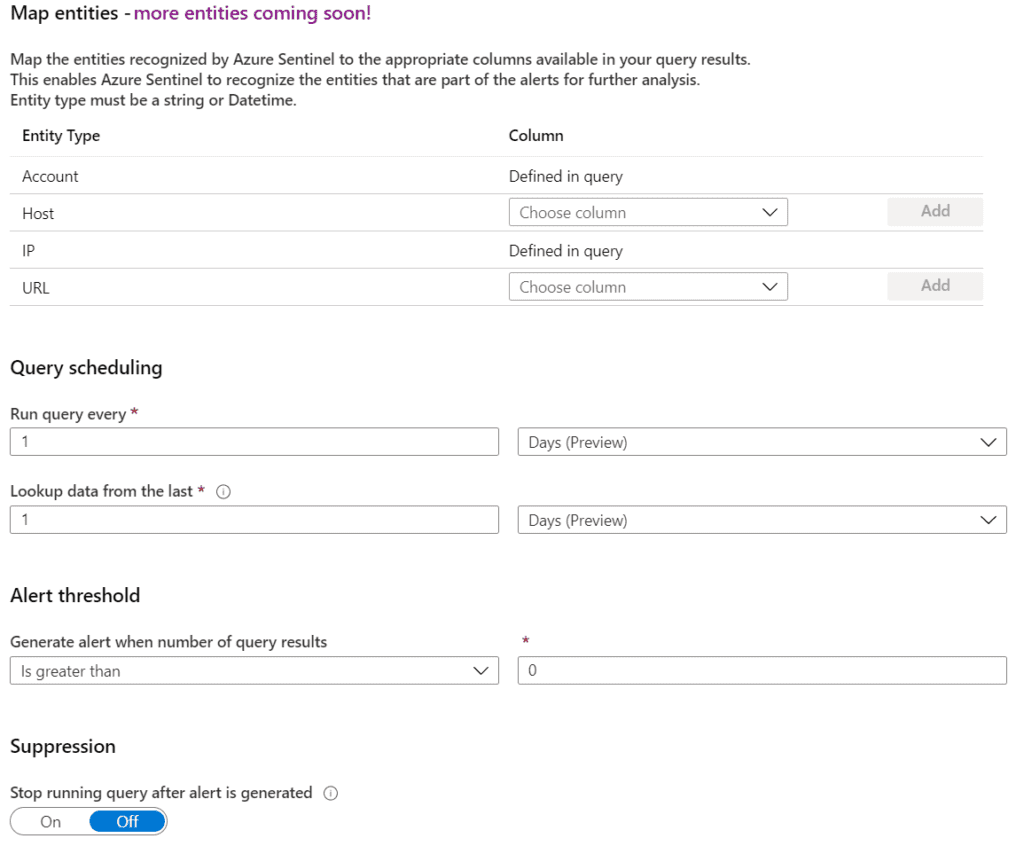
During the creation of a template or custom analytic rule, you can configure specific settings to create an appropriate schedule and alert threshold. You can specify how often to run the query and how far back to search. In addition, alert threshold specifies how many results are required to issue an incident alert.
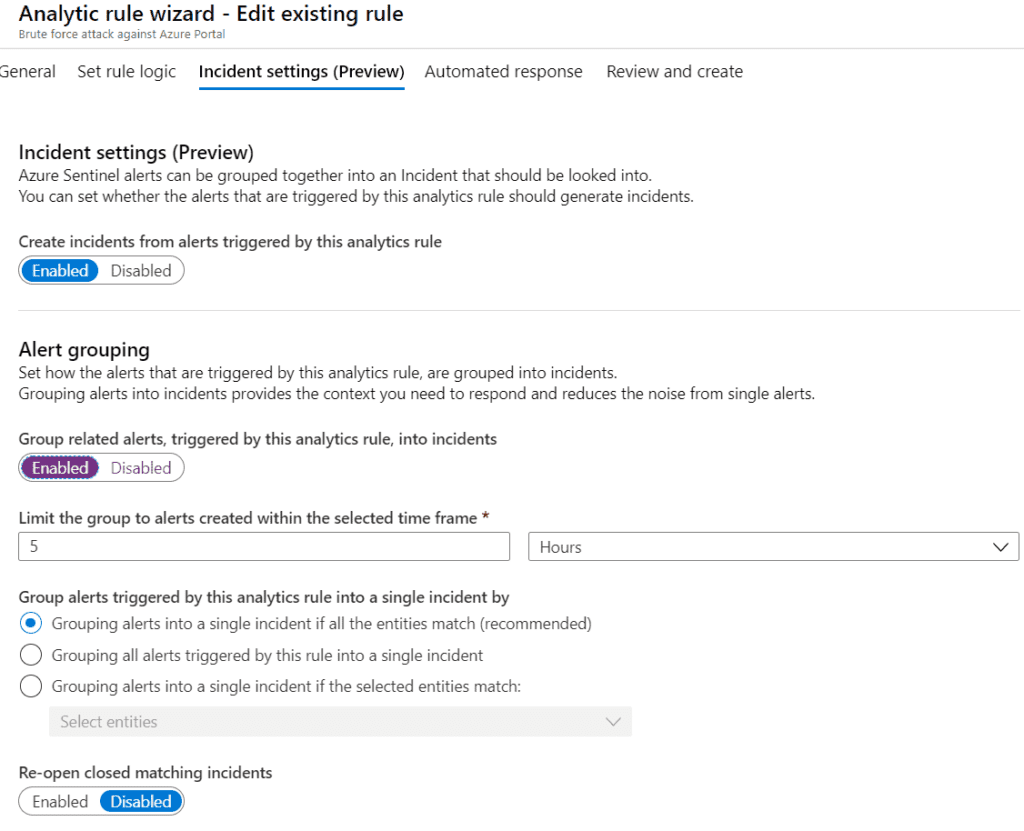
Finally, you can assign a playbook for automated remediation or actions against the results. More details about playbooks are below.
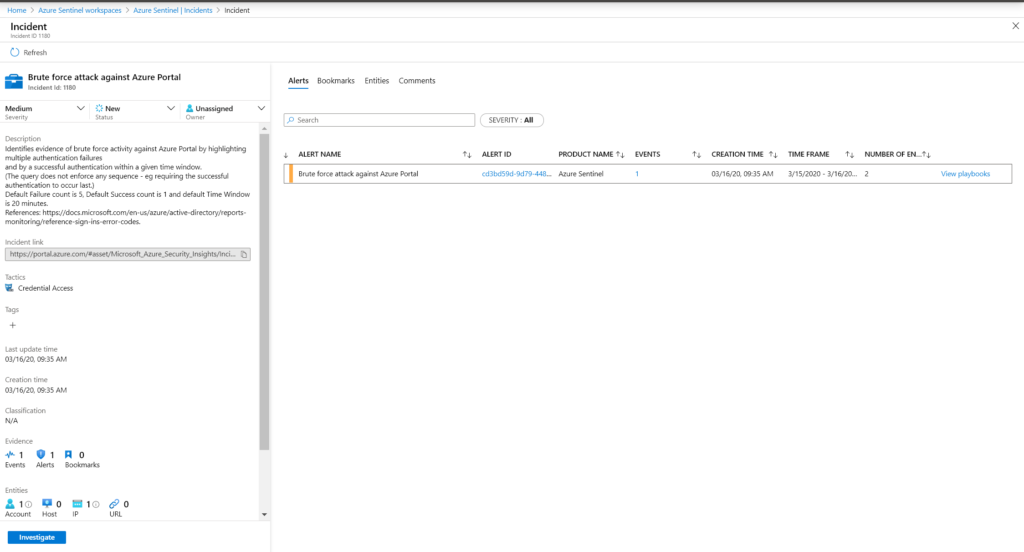
Incidents
Incidents are only created when specified by an analytic alert rule. In the Azure Sentinel Portal, click on Incidents to view a list of all incidents created. Clicking on View full details provides additional information on the incident. You can change the severity, if applicable, set the Status, and assign the incident to the responsible individual to investigate further. You can also manually submit the results of this incident against any playbook created for Azure Sentinel.
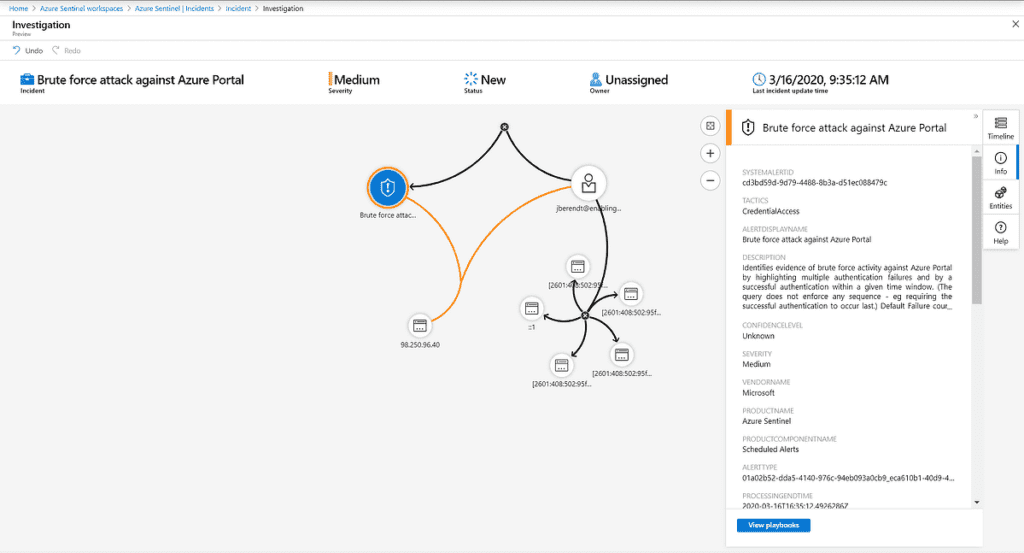
Currently in preview, clicking on Investigate provides the Investigation Graph. This provides an interactive overview of all entities involved in the incident. This will assist to understand the scope and impact of the incident, determine a root cause, and stop any potential threats that may be occurring elsewhere.
Incidents
Playbooks are Azure Logic Apps, but specific for Azure Sentinel by adding an API connection to Azure Sentinel alerts. The example playbook below sets and Microsoft Entra ID (formerly Azure AD) user account to disabled when an alert is triggered and puts a comment into the Incident. Additional actions can be added, such as a simple email notification. Anything that Logic Apps can connect to, you can tie it into an Azure Sentinel Playbook and Analytic Rule to automate that action.Microsoft Entra ID (formerly Azure AD)
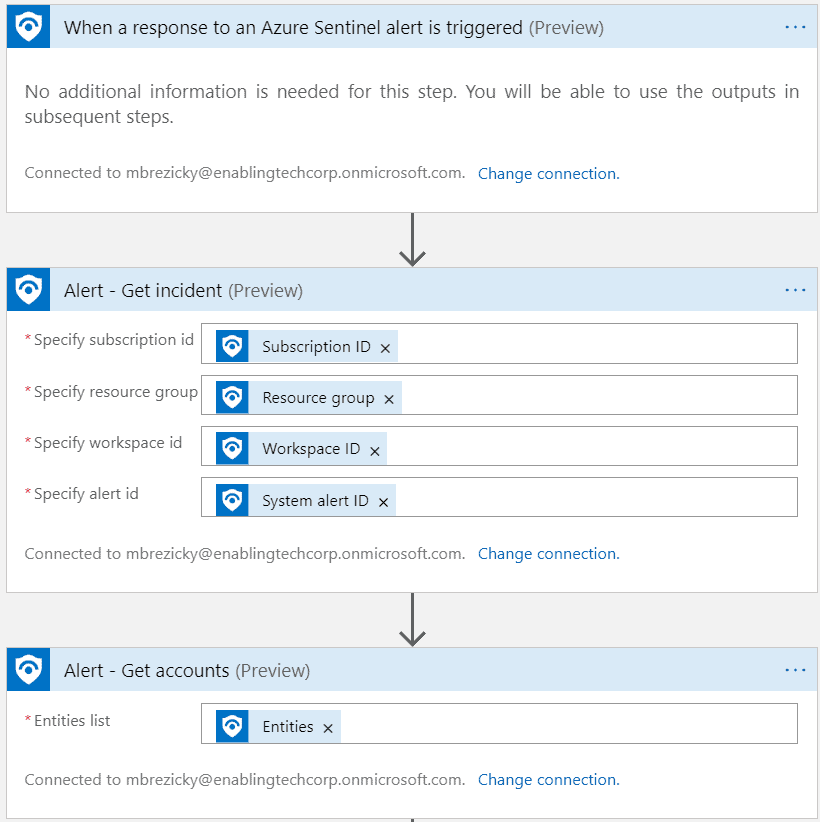
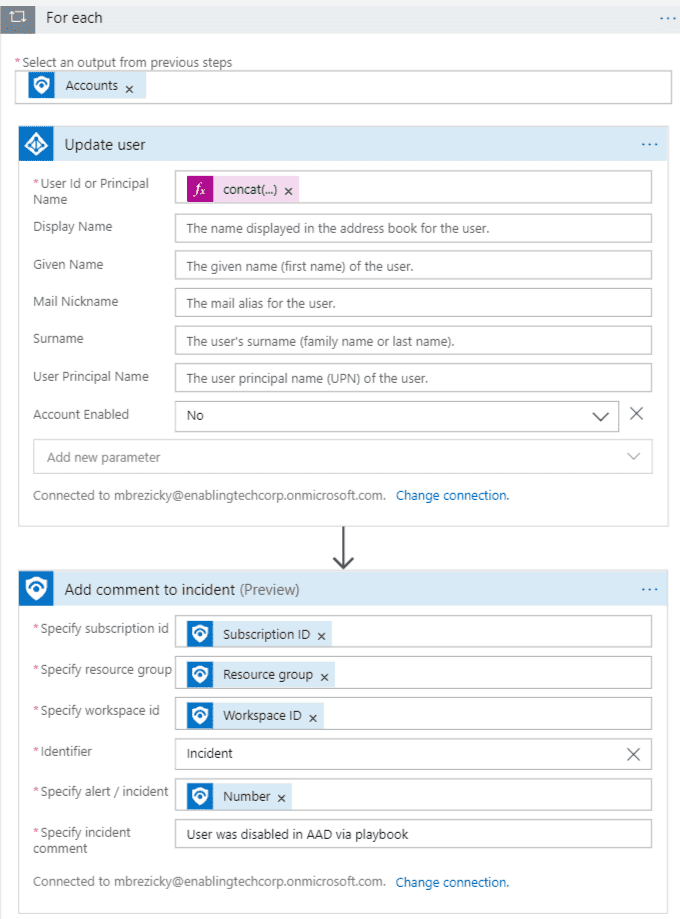
This has been a small sample of the capabilities of Azure Sentinel. Azure Sentinel can be extended in many ways to manage and monitor your environment. You can integrate Azure Sentinel into an existing Splunk deployment or deploy it as Infrastructure as code using DevOps. Azure Sentinel can be used in conjunction with Azure Lighthouse to manage and monitor multiple Azure environments allowing eGroup | Enabling Technologies the ability fully manage your Azure Sentinel deployment and ongoing operations and incident response.
eGroup | Enabling Technologies can help you properly prepare for moving to the cloud based on Microsoft Best Practices and utilizing a secure and productive environment. Contact our team of experts today for assistance on moving to the cloud!
Last updated on August 3rd, 2023 at 01:29 pm