New Microsoft Defender Security Tools: MDEASM and MDTI

Cybersecurity is ever-changing. New attacks and techniques are practically created every day. Organizations are getting more complex with multi-cloud environments. Data is exponentially growing and we are losing visibility into our assets due to poor governance. Last week, Microsoft announced two new Defender solutions as a result of their acquisition from RiskIQ.
Microsoft Defender External Attack Surface Management
Microsoft Defender External Attack System Management (MDEASM) is a continuous discovery solution to map out an external view of your organization. Too many security assessments focus on vulnerabilities and controls inside their organization, whether that be their cloud tenant or behind a firewall. The solution is built directly in Azure and can be deployed as easily as any other Azure resource.
MDEASM will discover and assess from the following categories:
Once discovered and assessed, there are four dashboards to view your reports:
Microsoft has attempted to preconfigure many organizations external attack surface. If your organization exists, you can quickly access your inventory in minutes.
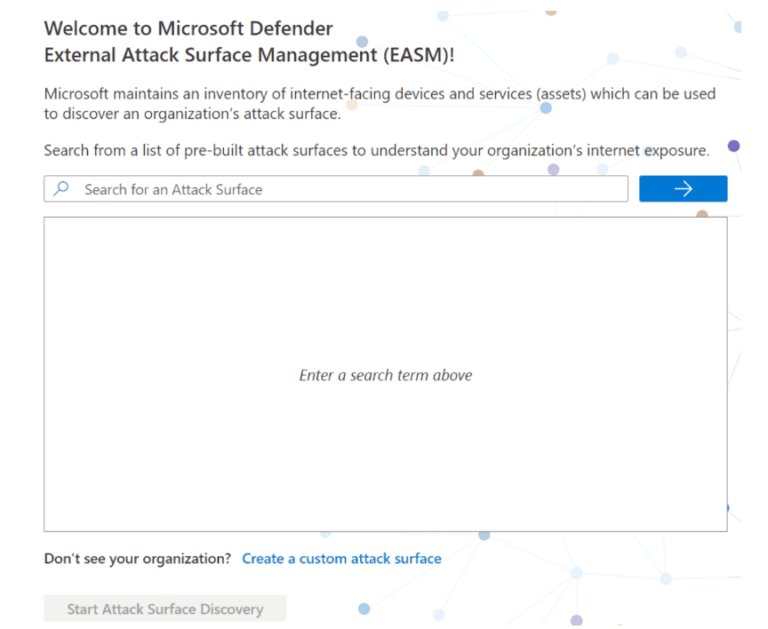
If your organization is not in Microsoft’s pre-built database, you can create a custom Attack surface discovery. Simply enter specific information you know about your organization in one or more respective categories. The more information you provide, the more extensive the discovery will be. Additional items be added later for further discovery. Also, multiple discovery groups can be created to keep responsibilities or certain external assets separate.
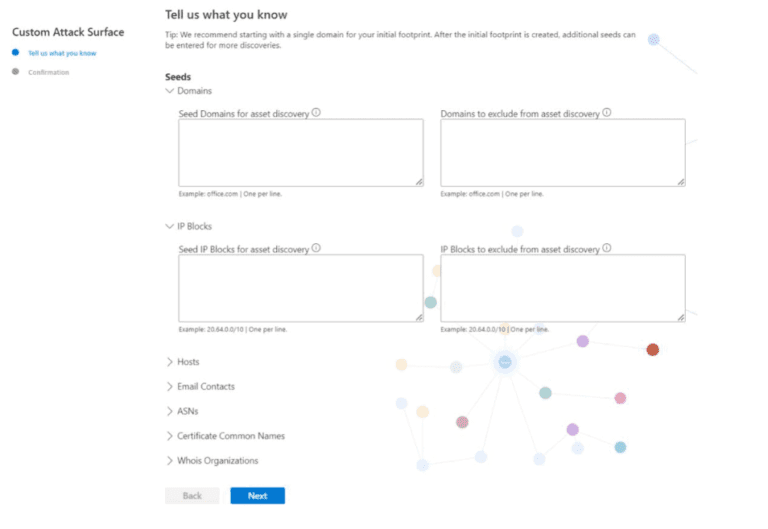
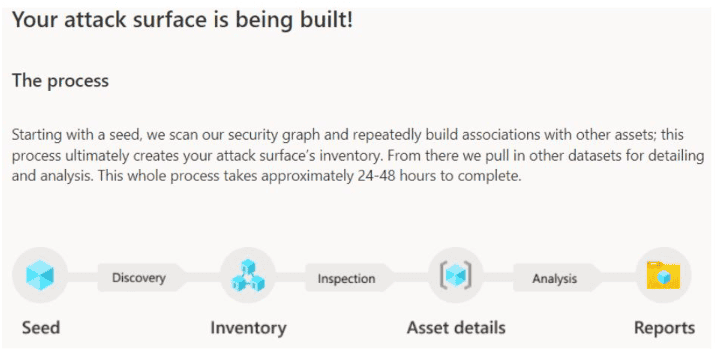
Once you select or define the seed criteria for discovery, Microsoft will scour and crawl throughout the Internet to pull in related assets and provide an inventory of your discovered assets as well as an attack surface and security posture assessment. The discovery can take 24-48 hours according to Microsoft.
Microsoft Defender Threat Intelligence
Microsoft Defender Threat Intelligence (MDTI) is a real time threat intelligence database that provides direct access to Microsoft’s security signals.
You can access MDTI by going to https://ti.defender.microsoft.com/. Currently, there are no costs advertised, but there is most likely going to be a free tier and PUPM license add-on. Having a free tier will greatly increase adoption of this service allowing organizations to have an additional consolidated resource for threat hunting. I presume the paid tier will allow for automation and integrations to solutions such as Defender for Cloud and Microsoft Sentinel.
From the home page, analysts can use the search box to lookup specific Indicators of Compromise (IOCs), such as DNS data, IP Addresses, suspicious domains, etc. You can also use the searching capabilities to look up your own assets to gather information about your own attack surface, complimenting what MDEASM will discover.
Also on the home page are threat intelligence articles that provides descriptions of the threat as well as public and Microsoft added indicators.
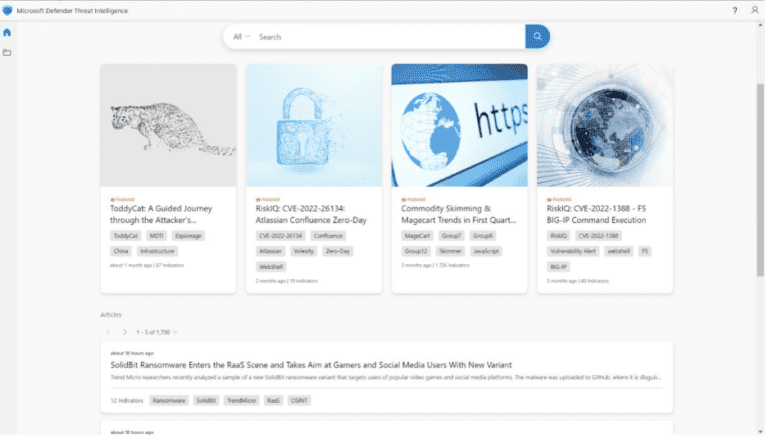
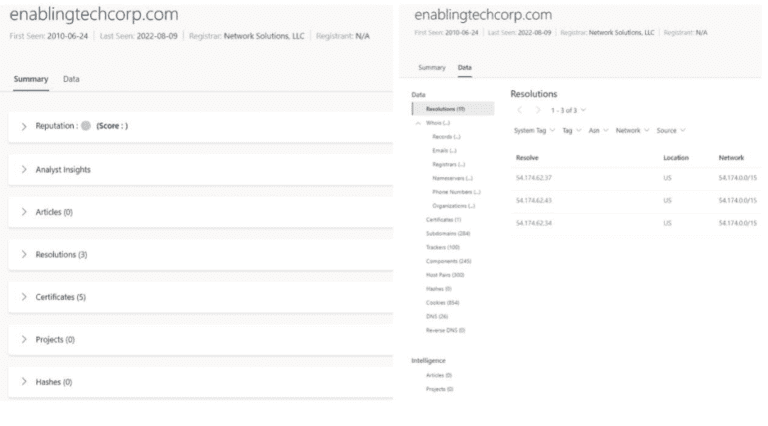
When searching for data or indicators, Microsoft provides both a Summary view and advanced view of the data set associated with that indicator/artifact.
In the ever-changing world of cybersecurity, MDEASM and MDTI are two great new tools to add to the Defender suite. While full pricing details haven’t been announced yet, I see these two tools being heavily adopted to have better visibility into an organization’s assets. If you don’t know what you have, how can you know what to protect? In future articles, I will go into a much deeper technical details for each respective solution.
eGroup can help you properly prepare for moving to the cloud based Microsoft Best Practices and utilizing a secure and productive environment. You can check out more in the Security section of our website.
Work with our team of Cloud Computing Consultants who have “been there done that” multiple times to know all of the “minefields” to prevent missteps.

Senior Cloud Solutions Architect - Microsoft
Last updated on July 31st, 2023 at 11:32 am