If you choose a capacity reservation, you are charged a fixed fee up to the capacity limits. If you exceed the chosen capacity, you are charged the per GB rate over the capacity.
The Pay-as-you-go rate is ideal for initial deployments, smaller organizations, or if you do not know how much data you will need to ingest. It takes between 65-70GB of data within the Pay-as-you-go model to match the costs of the 100GB/day capacity. You can increase or decrease your capacity at any time.
There are several free elements as well including:
- First 31 days of Azure Sentinel
- 90 Day retention ($0.12/GB/Month after 90 days)
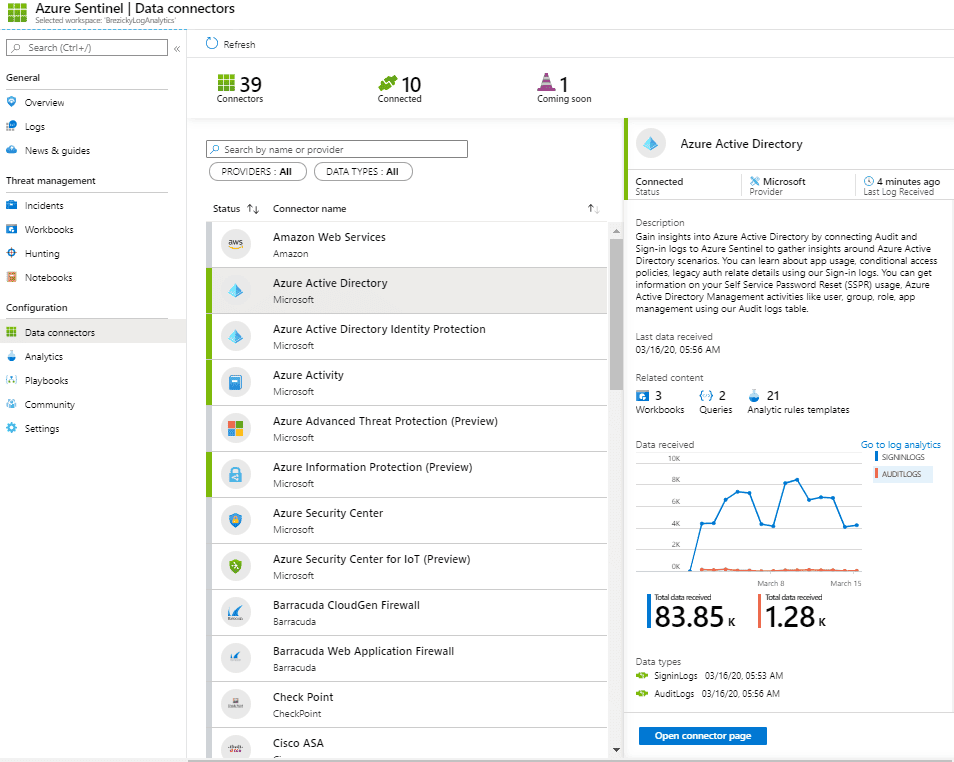
- Microsoft Data source ingestion*:
- Azure Activity Logs
- Office 365 Audit Logs (all SharePoint activity and Exchange admin activity)
- Microsoft Threat Protection products:
- Azure Security Center
- Office 365 ATP
- Azure ATP
- Microsoft Defender ATP
- Microsoft Cloud App Security
- Azure Information Protection
*Microsoft Entra ID (formerly Azure AD) data is not free.
Azure Sentinel may be the newcomer to the SIEM world; however, it is quickly becoming a top tier solution due to its cloud native design. Microsoft has made a significant investment into this service and has all intentions of driving its capabilities above and beyond what competitors offer. With the ease of deployment, minimal to no cost initial integrations into Microsoft services, and familiar Azure interface, Azure Sentinel provides the means for any organization to have a SIEM solution.
In the next article on Azure Sentinel, we will take you through the process of initial setup and onboarding data sources to Azure Sentinel. If you’d like assistance, eGroup | Enabling Technologies can help you properly prepare for moving to the cloud based on Microsoft Best Practices and utilizing a secure and productive environment.